This post was originally published by me on www.sentialabs.io, it has been slightly adapted to better fit my personal site.
When you manage many AWS accounts, you might quite often need to login to the AWS Console of those accounts. We wanted to provide a way to access the AWS Management Console that was both secure and easy to use.
Options for AWS Console Authentication
We have looked at a couple of options (see table) for authentication to the AWS console:
- Shared root credentials: Using a system like 1Password or LastPass the root credentials of all AWS accounts could be shared. This means that everybody has full privileges within all AWS accounts. A person leaving the team requires all credentials to be rotated. Requires one MFA token per AWS account.
- Personal IAM Users: Each person could have its own IAM user in every AWS account. User actions can be audited. IAM policies can be used to finetune user privileges. A person leaving the team requires all its IAM users to be deleted. Requires one MFA token per user per AWS account.
- Personal IAM Roles: Each person could have its own IAM role in every AWS account, using a single IAM user to assume this role. User actions can be audited. IAM policies can be used to finetune user privileges. A person leaving the team requires only one IAM user to be deleted. Requires a single MFA token per user.
| Shared Root | IAM Users | IAM Roles | IAM Roles & Locksmith | |
|---|---|---|---|---|
| Security | ||||
| No shared credentials | ❌ | ✅ | ✅ | ✅ |
| No shared MFA | ❌ | ✅ | ✅ | ✅ |
| User policies | ❌ | ✅ | ✅ | ✅ |
| Auditability | ❌ | ✅ | ✅ | ✅ |
| Ease of Use | ||||
| Single MFA | ❌ | ❌ | ✅ | ✅ |
| Simple Login | ❌ | ❌ | ❌ | ✅ |
| Conclusion | 🙈 | 😫 | 😉 | 😍💕 🍻🎉 |
Of these options we found using IAM Roles to be the most secure, but logging into the AWS Console using IAM Roles is quite a hassle, therefore Locksmith – a Chrome Extension for AWS Console login using Cross-Account IAM Roles – was created.
What does it look like?
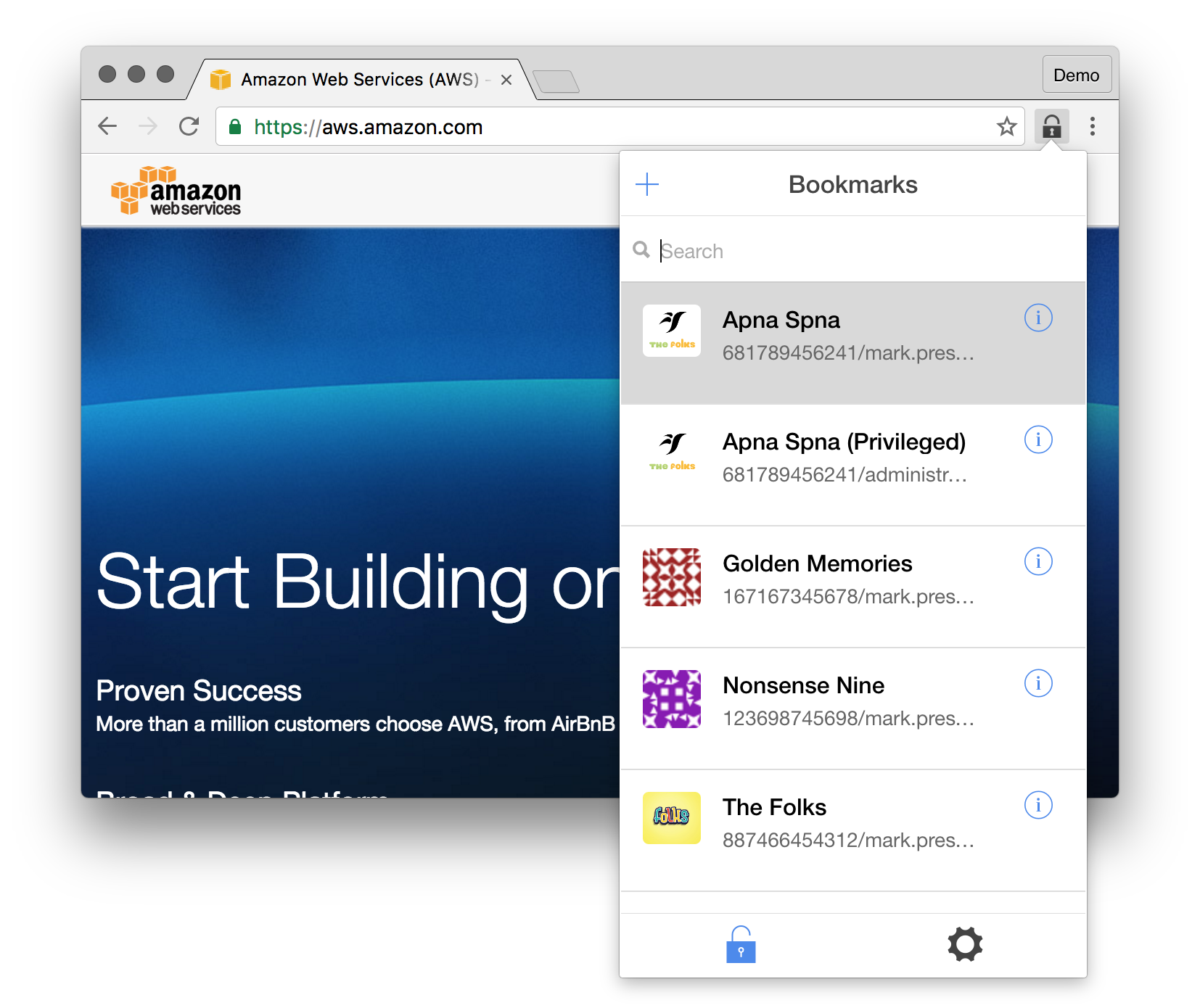
How does it work under the hood?
We use a single IAM user per person. This user has a single MFA, and you can easily remove the IAM user to revoke a person’s access to all accounts.
- Assume a role using the user’s personal IAM User credentials
- Obtain a a sign-in token from the AWS Federation service
- Construct a sign-in URL
- Open the sign-in URL in the webbrowser
But, wait a minute…
…doesn’t the AWS Console support this already?
Yes indeed, we developed Locksmith before AWS announced this feature. Even so, we still might have developed Locksmith since it has the following advantages over the tool built into the AWS Console:
- The list of accounts is not limited to the last five you accessed
- Supports MFA for assuming the cross-account role
- Consumes an API to present an up to date list of your AWS accounts
- Quicker, you don’t have to login to your personal AWS Console first
- Shows the name of a bookmark (AWS account), not that of the assumed role